General Information
Commix (short for [comm]and [i]njection e[x]ploiter) has a simple environment and it can be used, from web developers, penetration testers or even security researchers to test web applications with the view to find bugs, errors or vulnerabilities related to command injection attacks. By using this tool, it is very easy to find and exploit a command injection vulnerability in a certain vulnerable parameter or string. Commix is written in Python programming language.Disclaimer
The tool is only for testing and academic purposes and can only be used where strict consent has been given. Do not use it for illegal purposes!!Upload Shells
Commix enables you to upload web-shells (e.g metasploit PHP meterpreter) easily on target host. For more, check 'upload shells' wiki page.Modules Development
Do you want to increase the capabilities of the commix tool and/or to adapt it to our needs? You can easily develop and import our own modules. For more, check 'module development' wiki page.Command Injection Testbeds
A collection of pwnable VMs, that includes web apps vulnerable to command injections.- Damn Vulnerable Web App (DVWA)
- Xtreme Vulnerable Web Application (XVWA)
- OWASP: Mutillidae
- bWAPP: bee-box (v1.6)
- Persistence
- Pentester Lab: Web For Pentester
- Pentester Lab: CVE-2014-6271/Shellshock
- Pentester Lab: Rack Cookies and Commands injection
- Pentester Academy: Command Injection ISO: 1
- SpiderLabs: MCIR (ShelLOL)
- Kioptrix: Level 1.1 (#2)
- Kioptrix: 2014 (#5)
- Acid Server: 1
- Flick: 2
- w3af-moth
- commix-testbed
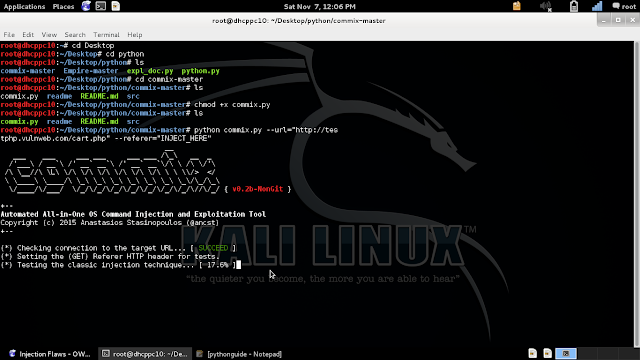
download link : https://github.com/stasinopoulos/commix



No comments:
Post a Comment